Our products WLSDM and WL-OPC are not affected from Apache Log4j Security Vulnerabilities (CVE-2021–44228).
We are not using any log4j library. Also, our security layer is protected by default Oracle WebLogic security layer just as WebLogic Administrator console. Oracle WebLogic is not using Apache Log4j by default settings. Default “Oracle WebLogic Logging Service” is JDK. But, log4j is also another option for Oracle WebLogic Logging Service infrastructure. If you have changed this configuration as Log4j you need to take action. Oracle published official support link for “CVE-2021–44228” security bug.
Security Alert CVE-2021–44228 / CVE-2021–45046 Patch Availability Document for Oracle Fusion Middleware (Doc ID 2827793.1)
From Oracle Document: “Apache Log4j version 2 is not used in default Oracle WebLogic Server installations or configurations. However, the Oracle WebLogic Server home contains vulnerable Log4j version 2 jars.”
Here is the development report from our Software Architect, Mustafa Şensoy.
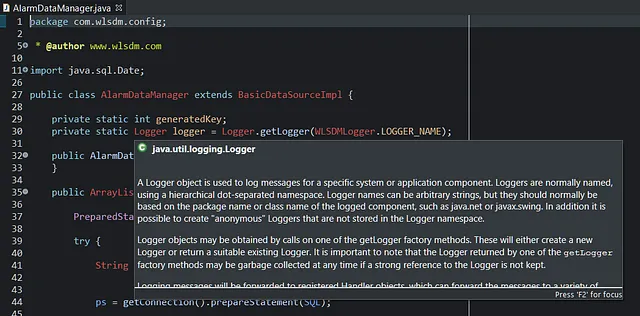
WLSDM Logger Strategy: WLSDM is not affected by Apache Log4j2 security vulnerabilities because our products WLSDM and WL-OPC use the “java.util.logging.Logger” as the logger.
Mustafa SENSOY
WLSDM/WL-OPC Software Architect
Do or do not there is no try!

WL-OPC’s SpringBoot infrastructure and package is shipped with vulnerable log4j2 jar library. WL-OPC is also not using log4j2 framework, too. Here is the SpringBoot official post: Log4J2 Vulnerability and Spring Boot
Fevzi Korkutata
CTO @ Volthread | Product Manager | Oracle ACE
https://linkedin.com/in/mfevzikorkutata